Evolution and sustainability of digital security tools: An exploration of F/LOSS encrypted chat apps
Team Members
Becky Kazansky, Frederike Kaltheuner, Anne-Sophie Letellier, Lonneke van der Velden, Stefania Milan, Davide Beraldo, Carlo De Gaetano, Emile den Tex, Sebastian Benthall, Donato Ricci
Introduction
Chat apps have changed our way of communicating with friends and family. In 2015, messaging apps surpassed social networks for number of users (McKitterick, 2016). People use chat apps to call, make calls, access and exchange content. Whatsapp is by far the most popular chat application, with about 1 billion active monthly users, followed by Facebook Messenger with 900 (Statista, 2016). Until recently, however, chat apps potentially exposed users to monitoring and surveillance. In April 2016, Whatsapp announced that it will support encryption across all its apps, in a move that have been defined a ‘landmark event’ for privacy protection (Meyer, 2016). But the idea of encrypted communications in chat apps emerged in the realm of open source software (FLOSS). Examples of Free Libre Open Source tools include Jitsi and Signal. The difference between these proprietary applications and F/LOSS applications is characterised by a number of important controversies: (1) the claims of tools being private and secure are contested on an ongoing basis. Tools such as Jitsi and Signal have a better reputation amongst many in the technical community because their code can be reviewed and audited to see if developer claims stand up to the rhetoric. But Jitsi and other FLOSS tools are often critiqued for being difficult to use, or for breaking due to a lack of resources to keep projects and communities involved in their development and maintenance. They often have small teams, relying on extremely limited to no funding, with decades-old parts that haven’t been updated. (2) One controversy in the technical community relates to Signal. One prominent new tool called Signal is lauded both for its ease of use and the trust the technical community. Signal has come into public awareness recently with recommendations for its use from Edward Snowden and other prominent privacy advocates. Signal has recently begun contributing to the infrastructure of closed, commercial tools such as Whatsapp. Now, Whatsapp is owned by Facebook, which is known for its dubious policies, selling user data to third parties and governments.This situation presents an important dilemma: with the integration of the Signal protocol into Whatsapp, strong encryption becomes available and accessible to millions of people. Yet the metadata of users is still exposed to a large corporation and third parties. Additionally, as
Signal has become a product, its lead developer has written that he sees less importance in federating its infrastructure with other free and libre open source tools, breaking both a formal and informal code among free libre open source developers. In part, the controversies with Signal might be due to the fact that the small resources available to FLOSS tool development is now being channeled away into the work of large companies. As researchers interested in tracing the evolution of sociotechnical infrastructures, we argue that the evolving ecosystem of chat tools offers a great opportunity to develop DATACTIVE's 'infrastructure ethnography' both in method and object of study.
Research Questions
How has the 'post-OTR (Off-the-Record)' ecosystem of encrypted FLOSS chat applications evolved in its configuration and maintenance?
Sub questions:
1. What is the encrypted F/LOSS chat application ecosystem?
2. What is the configuration of the community around encrypted F/LOSS chat apps on Github?
3. How are individual encrypted F/LOSS chat applications maintained?
Methodology
We conducted a data infrastructure ethnography (following Star, 1999) which combined a computational and qualitative analysis. We studied the configuration of the ecosystem by looking at how code, protocols and people relate together. We studied maintenance by tracing the changes and commits in Github repositories of the applications selected for our study.
Our research relies on two types of datasets.
1) The Github repositories of the following encrypted and F/LOSS chat apps
| Repository name | Group | |
| 1 | adium | adium |
| adium | obeattie | |
| 2 | ChatSecure | venil |
| ChatSecure-iOS | ChatSecure | |
| ChatSecure-Push-Server | ChatSecure | |
| ChatSecureAndroid | the guardian project | |
| 3 | cryptocat | cryptocat |
| 4 | jitsi | jitsi |
| 5 | LibreSignal | LibreSignal |
| 6 | np1sec | equalitie |
| 7 | Pidgin | kitsonk |
| Pidgin | rosedu | |
| Pidgin | tieto | |
| 8 | ricochet | im |
|
9
| Signal-Android | whisper systems |
| Signal-iOS | whisper systems | |
| Signal-desktop | whisper systems | |
|
10 | Silent text | Silent circle |
| Silent text android | Silent circle | |
| 11 | surespot-android | surespot |
| surespot-ios | surespot | |
| 12 | threema | threema.ch |
| 13 | tor-messenger | TheTorProject |
2) Online textual material featuring encrypted and F/LOSS chat apps.
Operationalisation per sub question:
1. What is the encrypted FLOSS chat application ecosystem?
1.1 Review of popular literature in order to sketch the FLOSS chat application ecosystem.
Read articles related to the following themes: Encrypted chat applications, FLOSS and the context of controversies around encrypted chat applications.
1.2 Trace the dynamics (or ‘ecology’) of encrypted chat apps by tracing the change of expert recommendations.
2. What is the configuration of the community around encrypted F/LOSS chat apps on Github?
We approach this question in a twofold way. Firstly, through tracing at how people relate to (shared) projects (2.1), and secondly, through looking at how projects relate to (shared) code (2.2).
2.1 Analyse the collaboration on github projects: Analyse whether top contributors also collaborate on other projects together (in other words: look at whether they have shared interests) by using the DMI tool for scraping GitHub repositories
We first compiled a list of expert recommended encrypted F/LOSS chat apps that are on GitHub as starting points for our study into the configuration of the ecosystem.
We used an ‘expert list’, an EFF report rating messaging apps ( EFF secure messaging scorecard), and selected those that were encrypted and F/LOSS. We then selected those that were on Github including the various versions that exist for different operating systems. Because the EFF rating is in updating phase, we did a google query ‘encrypted chat apps’ to extend this list and asked for confirmation with a security expert.
We then used the DMI Github Contributors Scraper and scraped the contributors for the different versions of the apps. We selected all contributors that made more than 5 commits as ‘top contributors’. We compiled a CSV-document with top contributors and their projects. We used the Médialab ‘Table 2 Net’ tool (http://tools.medialab.sciences-po.fr/table2net/) to see which contributors contribute to which projects and visualised this with Gephi (using the following settings: XX).
2.2 Visualise code-dependencies: Analyse the federation of infrastructure by looking at which apps share lines of code
We took our list of encrypted chat apps and the different versions and we looked up their technological dependencies such as the required operating system, coding languages, encryption protocols, and networks. Because the read.me files were usually incomplete, we delved into the (history of) Github, Wikipedia, we browsed their repositories, homepages, and Google.
We compiled a file listing the apps and their corresponding technological dependencies, and marked down when there were crucial moments in which technological dependencies are abandoned or absorbed.
For example, Axolotl is a cryptographic software protocol. It was itself an improvement of OTR and XMPP. The Axolotl protocol got modified and rebranded into Signal. This is an absorption. Another example: the Redphone app used the Redphone protocol. The Redphone app is no longer available but it is also absorbed into Signal. So in Signal the 'Redphone Protocol' got both inherited and abandoned.
3. How are individual encrypted FLOSS chat applications maintained?
Maintenance is central to the security, and thus continued existence of encrypted chat application. For the purpose of this study, we operationalise maintenance as “commits” to the Github repository. On Github a “commit” is an individual change to a file (or set of files). Every time a revision or change is saved, it creates a unique ID that allows you to keep records of what changes were made when and by whom. Thus defined, frequent commits are a necessary though not a sufficient criterion for proper maintenance of a tool. It is a gross indication of recurrent activities. In addition to measuring the total number of commits, we also measured which users were responsible for the monthly total number of commits. This distribution indicates how distributed the activities of contributors is, or in other words whether most commits originate from a small group of users.
For answering this question we focused on Jitsi and Signal. We selected Jitsi because it represents a synchronous OTR application. We selected Signal because it is a chat app that represents a ‘post-OTR’ app which uses asynchronous encryption with new protocols.
We measured the number of commits over time as an indicator of maintenance.
We used Big Bang (https://github.com/nllz/bigbang/) to scrape the entire Github repository (Jitsi, Signal IOS, Signal Android, Signal Desktop) and produce a CSV-file that lists all the singular commits by contributor including a timestamp. We plotted the total number of commits per month in the form of a frequency count bar chart, where the x-axis represents months, and the y-axis the total number of commits. Each bar chart is again divided by the commits that were induced by individual contributors.Findings
1.The encrypted FLOSS chat application ecosystem
1.1 t.b.a. 1.2 t.b.a2. The configuration of the community around encrypted FLOSS chat apps on Github
2.1 The analysis of the collaboration on github projects suggests that there are little links between project contributors and projects. Most of the time people don’t work on more than one project. If they do its on a different version of the same project (different operating environment). Since all these applications respond to different goals it is reasonable to think that these people are working on different projects. On the other hand its important to note that they are definitely linked through their dependencies, since these apps rely on the same technologies. Contributors iterate on these different infrastructural parts (such as federated protocols). Also in this graph, you don’t see the number of commits.
graph 1: collaboration of individual contributors (see attachment for larger image)
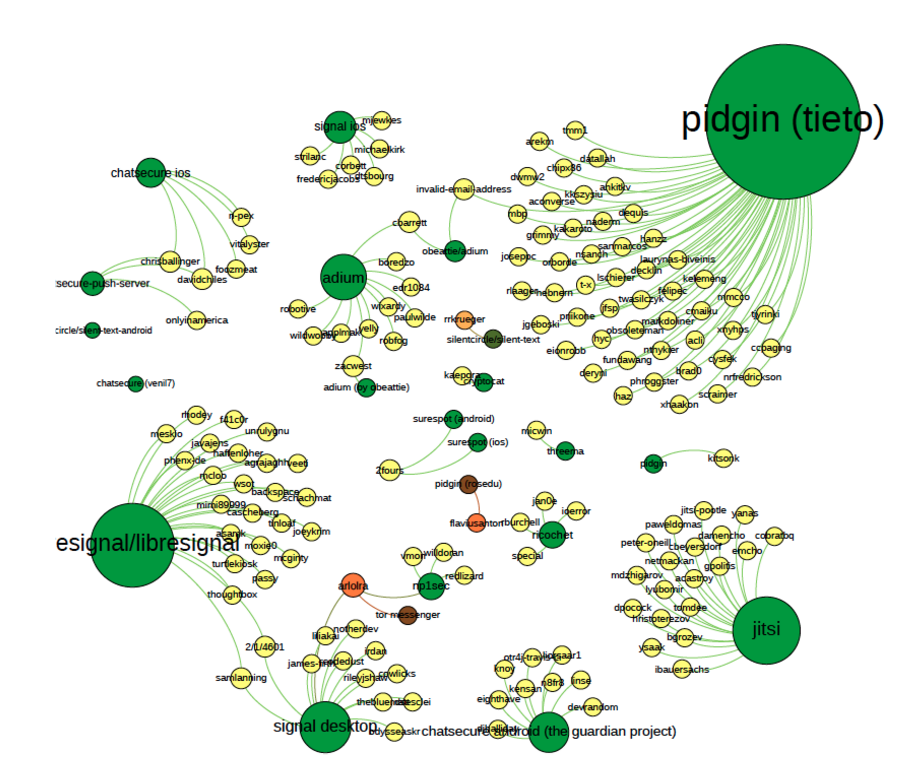
2.2 The visualisation of code-dependencies
graph 2: infrastructure dependencies (see attachment for larger image)
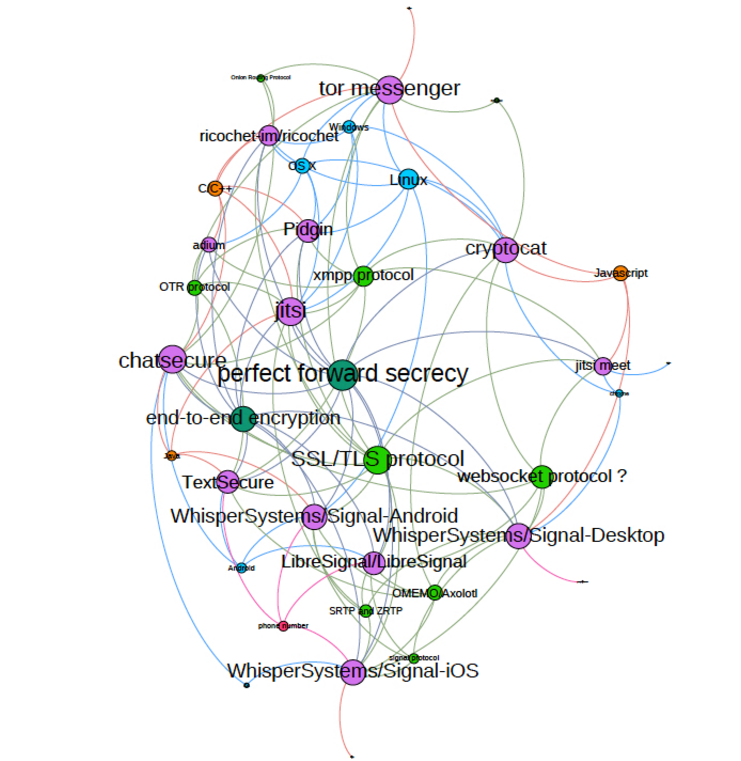
Pefect forward secrecy and end to end encryption are central cryptographic properties to the community. Jitsi appears to have many dependencies.
graph 3: infrastructure dependencies of FLOSS encrypted chat apps (see attachment for larger image)
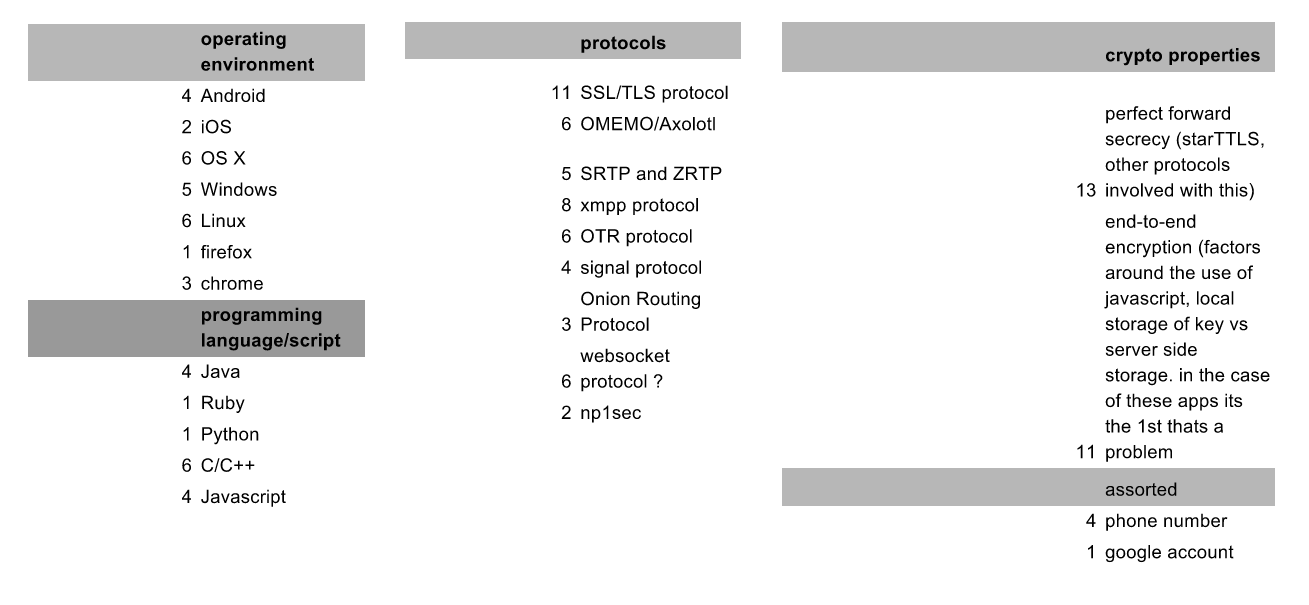
3. The maintenance of individual encrypted FLOSS chat applications
graph 4: maintenance of two encrypted chat apps over time: Jitsi, Signal IOS (see attachment for larger image)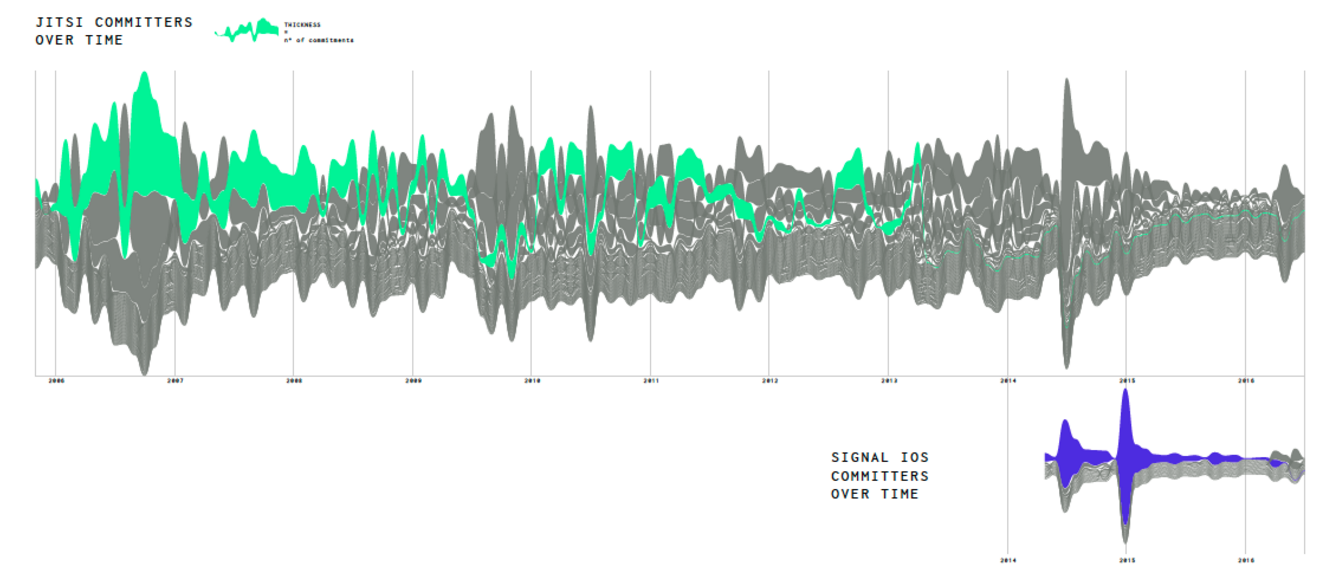 Graph 4 illustrates the maintenance of two encrypted chat apps over time. The first obvious finding is that the total number of commits vary greately over time and that few individial contributors play a substantial role in creating commits to the application. Additionally, some apps have more contributors than others; the much older jitsi for instance still have more commits that the newer Signal app for IOS. From the number of commits over time as an indicator of maintenance we see that apps have widly different numbers of commits.
We see a big spike around the time that Signal started working with Whatsapp. After that you see that graphs get smaller and smaller, but we don’t have an explanation right now for this. This would be an appropriate moment to investitate further through blog posts, issue discussions on github, and interview project contributors.
Graph 4 illustrates the maintenance of two encrypted chat apps over time. The first obvious finding is that the total number of commits vary greately over time and that few individial contributors play a substantial role in creating commits to the application. Additionally, some apps have more contributors than others; the much older jitsi for instance still have more commits that the newer Signal app for IOS. From the number of commits over time as an indicator of maintenance we see that apps have widly different numbers of commits.
We see a big spike around the time that Signal started working with Whatsapp. After that you see that graphs get smaller and smaller, but we don’t have an explanation right now for this. This would be an appropriate moment to investitate further through blog posts, issue discussions on github, and interview project contributors.
Discussion
Discuss and interpret your data for the reader, tell the reader of the implications of your findings and make recommendations.Conclusions
The research we did this week allows us to establish certain characteristics about the configuration and maintenance of our selection of encrypted FLOSS chat apps. A centrality of contributors but not infrastructures. It helped us identfiy points at which we would want to use other modes of inquiry/methodologies in our quest to develop a ‘digital infrastructure ethnography’
Bibliography
McKitterick, W. (2016). Messaging apps are now bigger than social networks. Business Insider, 15 June.
Star, S. L. (1999). “The Ethnography of Infrastructure”, American Behavioural Scientist, 34(3): 377-391
Statista (2016). Most popular global mobile messenger apps as of April 2016, based on number of monthly active users (in millions)
Meyer, D. (2016). Why WhatsApp's Encryption Embrace Is a Landmark Event, Fortune, 16 April
Appendix
Background reading on encrypted chat appsControversy between developers
https://whispersystems.org/blog/the-ecosystem-is-moving/
What is a federated protocol: https://stackoverflow.com/questions/22000264/what-is-a-federated-protocol
A criticism of signal on the basis of moving away from federation: http://blog.jonasoberg.net/is-this-the-end-of-decentralisation-2/
A critique of signal (tweet) https://twitter.com/pranesh/status/732239469198213121
A discussion thread arguing over signal contributions https://github.com/LibreSignal/LibreSignal/issues/37
A blog post from makers of a new tool, criticising signal https://medium.com/@wireapp/axolotl-and-proteus-788519b186a7#.xlz2pfczu
Tool comparisons/criteria
Comparison chart of different chat apps: https://en.wikipedia.org/wiki/Comparison_of_instant_messaging_clients#XMPP-related_features
EFF secure messaging scorecard: _ https://www.eff.org/node/82654_
Open integrity index https://openintegrity.org/metrics/
Bruce schneier's survey of encryption tools
Security in a box final tool selection and tool selection criteria
*DMI/big bang TOOLS BACKGROUND*
Background talk on the use of Big Bang:
_https://www.youtube.com/watch?v=AQFS_ES7rT0&ab_channel=Enthought_
_https://docs.google.com/presentation/d/1ZRRsw9jfthixc2JygWNR7R965_1vxTYRJU0QfK6CnoE/edit_
How to get started with big bang
- https://github.com/nllz/bigbang/wiki and research paper about Big
Bang _https://conference.scipy.org/proceedings/scipy2015/pdfs/sebastian_benthall.pdf_
- install git
- download data: read me of repository
| I | Attachment | Action | Size |
Date | Who | Comment |
|---|---|---|---|---|---|---|
| |
figure2.png | manage | 42 K | 15 Jan 2016 - 12:32 | AnneHelmond | Group of the Italian University websites tracked and the network of the trackers used. |
| |
figure1.png | manage | 45 K | 15 Jan 2016 - 12:32 | AnneHelmond | Presence/absence of trackers in Italian University websites |
| |
figure3.png | manage | 73 K | 15 Jan 2016 - 12:33 | AnneHelmond | Bubble chart of the typology of trackers used in Italian University websites |
| |
Screen_Shot_2016-08-22_at_19.59.34.png | manage | 82 K | 22 Aug 2016 - 18:00 | FridaKalt | Infrastructure Dependencies of FLOSS Encrypted Chat Apps |
| |
Screen_Shot_2016-08-22_at_19.59.41.png | manage | 362 K | 22 Aug 2016 - 17:59 | FridaKalt | Maintenance of encrypted chat apps over time |
| |
Screen_Shot_2016-08-22_at_19.59.22.png | manage | 398 K | 22 Aug 2016 - 17:58 | FridaKalt | Infrastructure dependencies |
| |
Screen_Shot_2016-08-22_at_19.59.13.png | manage | 470 K | 22 Aug 2016 - 17:59 | FridaKalt | collaboration of individual contributors |
Topic revision: 22 Aug 2016, FridaKalt
 Copyright © by the contributing authors. All material on this collaboration platform is the property of the contributing authors.
Copyright © by the contributing authors. All material on this collaboration platform is the property of the contributing authors. Ideas, requests, problems regarding Foswiki? Send feedback

